According to researchers at Singapore-based cybersecurity, investigation, and threat-intelligence firm Group-IB, phishing e-mails exploiting coronavirus panic accounted for only about 5% of all malicious e-mails detected and analysed by the Computer Emergency Response Team at Group-IB over the last few weeks. This relatively small percentage, they say, “can partly be explained by the fact that not all cybercriminals are capitalising on coronavirus fears”.
In fact, the eagerness of some black-hat hackers to use Covid-19 as a ruse to spread malware has created consternation in Internet’s darker alleys, as seen in exchanges on underground-Web forums.
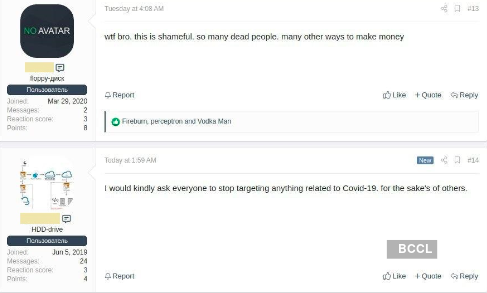
In a Russian-speaking underground forum, a hacker revealed that while the person initially had plans to use the pandemic to make money, that idea was dropped. “I decided to drop this idea. No good can come out of others’ tragedy…. At the start, I thought the same, that I would capitalise on the hype, but now when it became clear that it’s not just the panic, but the real tragedy, I suggest everyone not to exploit this unhappy event. I will also strongly urge my clients to switch from Covid-themed landings to some others,” the black-hat said.
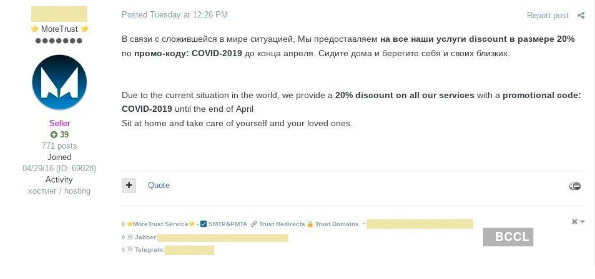
Just like in the mainstream economy, the underground economy too has been adversely affected by the pandemic. Group-IB says that its Threat Intelligence team “has tracked down more than 500 posts on underground forums in which users offered coronavirus discounts and promotional codes on DDoS, spamming, and other services to stimulate demand, affected by the pandemic”.
A few weeks ago, BleepingComputer, a technology website, had reported that many of the organisations engaged in ransomware it reached out to had said that they would try not to attack organisations engaged in health and medical care. A few of the groups they talked to even offered to share the key that will decrypt their data if any medical or healthcare-related organisation was at the receiving end of an attack.
That said, it is prudent for all organisations and individuals, both in healthcare and other sectors, to remain vigilant and follow best practices in not opening attachments and in updating their software, among other things.







